What is BYOK
BYOK is the acronym for Bring Your Own Key. It gives you the ability to use your own encryption key on your data in rest, so you are absolutely sure that no one else knows the key.
With PowerBI containing more and more data, and as such more and more sensitive data, it is no surprise that enterprises want to keep as much control over the decryption of that data in “the cloud” as possible.
Without BYOK, Microsoft manages the encryption keys for you, takes care of rotating them, backups, etc… When you bring your own, you become responsible for the management of those keys. You do also get the power to revoke the keys so no one can read any data from the capacity anymore.
How does it affect PowerBI
PowerBI BYOK will allow you to supply the key for encrypting datasets at rest. That’s all. At this moment.
This is not related to the license you have, but is only applicable to PowerBI Premium capacities (and derivates). A PowerBI Embedded is also a capacity in that sense, which you can acquire through Azure portal. And PowerBI Premium per User is in the background also a capacity, but read on before you think this comes with PPU.
Sounds to good to be true, so what’s the catch?
Nothing really, except maybe this:
You cannot disable it again (at this moment).
BYOK is enabled at tenant level by supplying your own encryption key (or keys), this step cannot be undone. That doesn’t mean that all of your PowerBI workspaces or capacities are going to use it.
- Activate : When you provide the key and specify the -activate switch, all your existing capacities and shared workspaces will be encrypted with this key. If you don’t specify it, the existing workspaces are not affected
- Default : When you add this switch, you tell your tenant to use this key for any of the newly created capacities. Another option to avoid, as it cannot be undone.
I’m sold, where do I turn this on?
PowerBI BYOK is different from M365 BYOK. It’s the same principle, but both are unrelated as they target different resources.
There is quite a bit of tedious setup going into it, but clearly documented here:
Bring your own encryption keys for Power BI – Power BI | Microsoft Learn
You basically have to perform following steps:
- Create an Azure Keyvault
- Give the Power Bi Service principle the proper rights to access the keyvault (Unwrap Key, Wrap Key)
- Create an RSA Key
- Configure Azure Keyvault firewall to allow trusted Microsoft services to bypass the firewall
- Enable BYOK at tenant level, by adding your encryption key to the PowerBI tenant by executing the PowerShell command
-
Add-PowerBIEncryptionKey - -Name : name of the encryption key
- -KeyVaultUri : Uri pointing to the KeyVault secret’s version (use only 4096 bytes keys)
- (optional) -Activate : will tell the tenant to encrypt any non-encrypted capacities with this key. Do you really want to do that?
- (optional) -Default : will tell the tenant to encrypt any future capacities with this key. This is really not a best practice. Don’t do it, as long as you can’t revert BYOK.
-
- Enable BYOK for the specific capacity you want it to be enabled for using
- Set-PowerBICapacityEncryptionKey
- -CapacityID : the GUID of the capacity
- -KeyName : the name of the encryption key
Summarizing the activation scenarios
Adding the encryption key without options
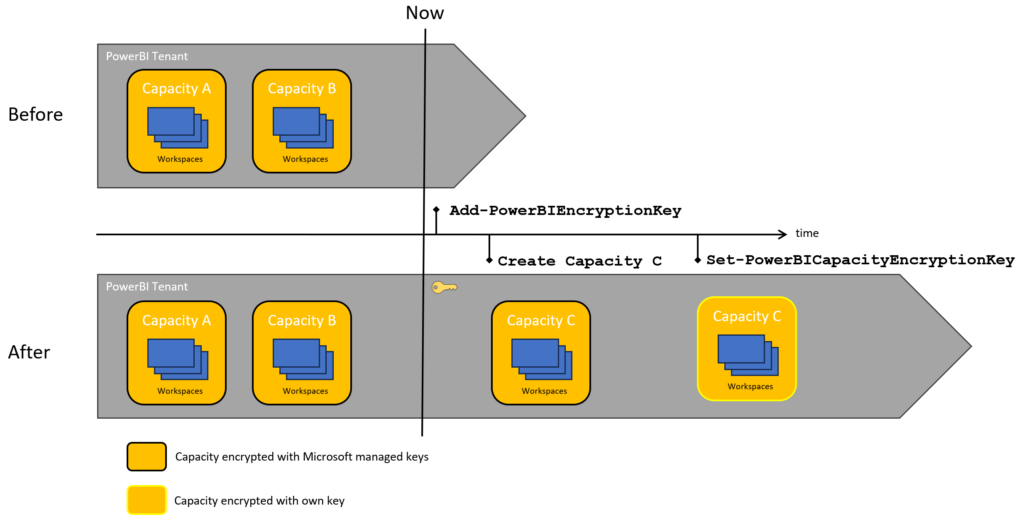
Nothing happens, the tenant will just know your encryption key, existing capacities are not using the key provided to the tenant.
When you add a capacity, it will not be encrypted with the key. You specify after creation to use the encryption key you added earlier.
Adding the encryption key with Activate
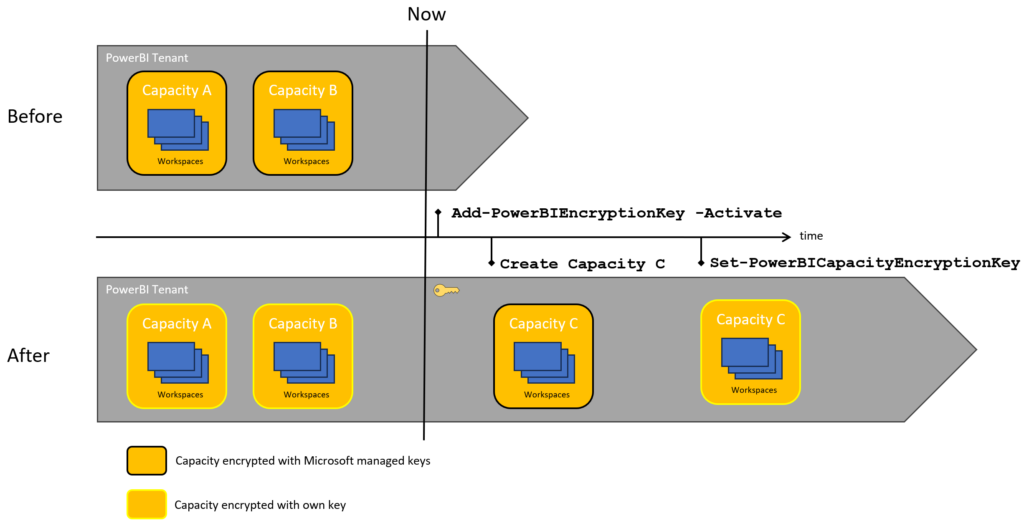
The existing capacities will all be encrypted with the provided key. New capacities don’t get encrypted with your key. You can set the encryption key after creation.
Adding the encryption key with Default
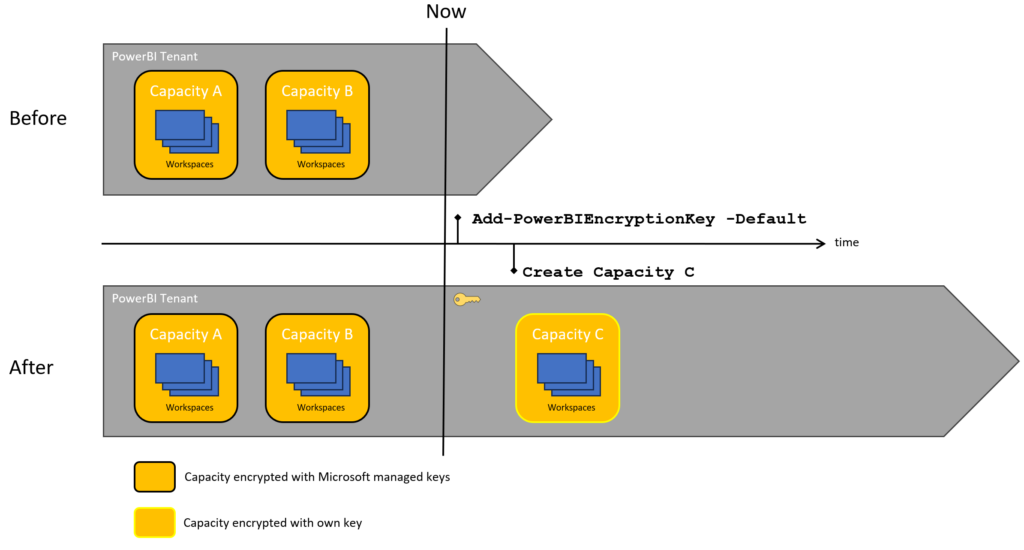
Existing capacities are left alone, newly created ones will get encrypted by… default.
I’m ready to do this, any last words?
It’s a good idea to enable this explicitly, for only those capacities you want to enable it. So, don’t use -Default and don’t use -Activate.
It’s also prudent to keep at least one capacity (or create one if you don’t have spare capacities) without BYOK. This way, you can move workspaces from BYOK-enabled-capacities back to Microsoft-managed-key-capacities. If you don’t have capacities without BYOK and it is enabled with -Default, you will never be able to revert.
PPU will only be able to use this, when you enabled BYOK with Default. As PPU is also a hidden capacity, in this way, this is a workaround to have BYOK for PPU “licenses”. But it comes at the cost of not being able to revert BYOK
Having your own keys is great and (if handled correctly) secure. But that comes at the cost of bearing the responsability to handle them correctly. You might have to implement a rotating key method, so that when the key becomes compromised, the capacities can be configured with another key, or even just as a precaution. Also… securing the keyvault securely, goes without saying.
There are some functionalities that fall outside of the BYOK scope. Following functionality of Premium capacities with BYOK will still use Microsoft managed keys, because the details are stored in the Home tenant, not in the capacity:
- Analysis Service Live connection
- Excel workbooks (except when importing them first in PBI desktop)
- Push datasets
- Streaming datasets
- PowerBI goals
Source: https://learn.microsoft.com/en-us/power-bi/admin/service-admin-premium-multi-geo